Why Cyber-resilient Backups Are More Important Than Ever
Time to read: 20 mins
Whether in casually passing a television in the office, an alerts notification, or an email roundup from a diligent New York publishing house, it is hard to escape headlines that spell out the impending crisis when a ransomware attack effectively infiltrates a business from the outside in. Whilst threat prevention is an advisable first line of defence, which includes popular security tools like Microsoft Defender, it is not the same as a cure to a ransomware attack.
Restoring mission-critical workloads with a backup strategy is the bedrock in understanding how your organisation can become even more resilient against modern day threat varieties. Without a reliable backup capability, a ransomware attack can be equal parts costly and devasting, slowing down a business’ pace of recovery.
What’s the true cost of being operationally offline? Reputationally, will my business ever recover? And what does a ransomware attack look like in financial terms? These questions may be hypotheticals to businesses who have blunted cyber attacks up until now, but they capture everyday anxieties that cause security leaders to lose sleep at night.
Backup and recovery best practices are more important than ever. Service downtime, customer upsets, and corrupted data – these are all just some of the common consequences that arise after a ransomware attack leaves a business offline.
Backup and Recovery: Best Practices
As ransomware becomes increasingly challenging, every organisation’s response plan should look to include backup and recovery. Whilst nothing new, backups can look and feel like a dated piece in a wider data protection strategy. Identify critical data, duplicate it, and store it securely. If you have seen this routine backup equation before, you might be missing one of the most important steps. Testing your backups, and ensuring copies are ‘clean’, makes the difference between a rapid recovery and one that’s halted by infected data.
The UK’s lauded National Cyber Security Centre (NCSC), which espouses regular security insights and musings across UK PLC, recently called attention to how ‘Backups really matter’. Observing the role of a backup capability in the event of a cyber incident, the NCSC recognises the urgency of restoring clean data for a rapid recovery of operationally critical work. But when best practice is wavered and backup plans fail to mitigate the infecting ransomware, even the most inspiring cyber security campaigns will fall flat.
Best practice is the safest means to ensure that your backup and restore capabilities can anticipate even the most aggressive cyber incidents by isolating copied, or duplicated workloads to a secure place.
Why You Need a Clean Room
In the scenario where your security leader has identified a cyber incident, struggled to contain it, but is now ready to start restoring corrupted workloads after a risk has been blunted, you need what’s called a “clean room”.
A “clean room” refers to a controlled and isolated environment where cybersecurity professionals analyze and safely handle malicious software (malware). These clean rooms are used to dissect and study malware specimens without risking their spread to other systems or networks.
Did you know… you must have a ‘clean room’ before you restore anything after an attack. This can be accomplished in two ways: the majority of solutions are run on physical hardware, but it can also be achieved in the cloud.
The clean room is the first (and perhaps most essential) step in your recovery after an attack. Recovered data must be isolated from the production network and then checked for malware again. As an easy oversight, and where backups are already infected, the damage will only compound over time whilst being offline.

This clean room process ensures that additional vulnerabilities, like Zero Day attacks, are not re-triggered, thereby infecting your workload again. A clean room is a forensic exercise in verifying that data re-entering production is ‘clean’ – that is, scrubbed from malware – and then it can be operationalised again.
How Do You Know If Your Data is Clean?
The most pressing, urgent, and time-sensitive task, following a suspected breach, is to remove any assumptions about the scale of the impact and how quickly you can recover. Many customers will use their own technologies and tooling to expedite the road to recovery. Over the years, CSI’s security and data protection specialists have experienced how aggressively malware can infect a whole IT estate, including data backups. If assumptions are made that backups are ‘clean’, this can substantially delay how quickly an operation recovers.
Our Head of Cyber Security, Leyton Jefferies, observes how clients need to invest not necessarily budgetarily, but more creatively into how they view and manage their backups.
“The road to recovery is fraught with untimely and costly security assumptions. Step back from the technical exercise of restoring infected data momentarily and look at backups conceptually. What do we know about backups? Clients will often have their own preferred methods for copying and securing data. But are they doing enough to forensically analyse the backups they create? The moment your business begins its path to recovery, if those backups have even a mild cold, rescuing a critical piece of your business might be just out of reach.”
For the best coverage, try restoring to new kit wherever possible. Why? Modern malware is creative enough to infect hosting hardware during an attack. It is a critical thought exercise to ask your security leader: how do I know if the data is clean? And where are you restoring to? If you are restoring clean workload to infected kit, traces of malware can reside, creating a vicious cycle where the infection spreads aggressively.
Customer Objections
Budgetary restraints have made even the most frugal and creative uses of cyber security tooling feel anticlimactic when a breach occurs. This is no different when considering how to clean and recover workloads after a ransomware attack.
Here’s how CSI illustrates the gap between backup best practices, a modern data protection solution, and where many customers might be making assumptions about the safety of their workloads:
In 2023, CSI gathered security leadership from different areas of the market in a single room to discuss relevant, urgent data protection and resiliency concerns. Addressing the audience, our specialists started with a straightforward question about procedural incident response planning: do you do backups? The consensus was that backups is a widely universal part of a data protection strategy.
We then asked, how often do you restore and test those backups? The room fell silent.
The moral of this thought exercise is how creative malware can spread because of innocent assumptions a business is making about how it backs up its data (and where it puts those copies).
In the same year, a retailer approached CSI to discuss ransomware prevention, but timing and budgetary limitations meant that the business had to delay onboarding a new, potentially critical, data protection solution.
Unfortunately, the retailer was eventually breached, and their existing security toolchain was insufficient in mitigating the infecting ransomware. CSI worked closely with the retailer to regain control and recover their critical workloads, but the journey was not simple.

Under the microscope, a ransomware infection was moving laterally across the business’ IT estate. This meant that backups re-entering the production environment were becoming quickly re-infected, creating a kind of destructive loop. The eventual scope of the damage become clear: the retailer’s infrastructure was wiped out. CSI leveraged a clean room to analyse and test the copies and ensure the data we recovered was safe.
Being operationally offline for any period of time, be it days, weeks, or longer, along with lost daily revenue, and reputational harm is now enough to severely damage any business, if not worse. In many cases, it’s more cost-effective to invest in cybersecurity tools than to pay for the costs of cleaning up a breach.
Simplifying how businesses can conceptualise the investment of a new cyber tool versus the costs of a breach, CSI’s Data Protection Lead, Ivor-John Ross had this to say:
“Firstly, don’t underestimate malware in the slightest. The innovation of modern-day malware packages we’re seeing now are more capable of discreetly infecting, spreading and multiplying.”
Ivor follows up by noticing how:
“When costs come into the total picture of your data protection strategy, then you should rally behind what we call a ‘minimum viable business’. Start by identifying your ‘crown jewels’, those workloads that are mission-critical to your business. Prioritise the protection of these workloads ahead of other areas of your business – recovering the most impactful systems first will limit, to an extent, the damage you take from a malware infection.”
Minimum Viable Business
There are a few ways that businesses test their backups. Backups often get confused with a kind of failover; or customers only conduct recovery testing for data integrity. The problem is that neither of these will prove that your business can recover from a ransomware wipe-out. This is a key part of strategising for the eventuality of a breach: are your backups proven and reliable enough to recover from a malware invasion?
A failsafe backup equation, if it existed, would look like this:

Large, complex workloads are the legacy of any scaling company. Importantly, to acknowledge the new age of a minimum viable business, leaders need to understand that not all workloads are the same. A retailer, for example, should prioritise its POS (point of sale) systems, because this impacts the daily gross profitability of the business. A minimum viable business is now, as Raconteur suggests, a knee-jerk reaction to leadership wanting to envision a more resilient version of their company. A minimum viable business, in fact, is the by-product of an organisation’s understanding about its business continuity and disaster recovery.
A minimum viable business is waiting at the end of a single question: what’s worth saving after a breach occurs?
In a post-pandemic, economically downturned world, it is becoming harder to clean data. In large part due to the volume of data produced every minute; paring down this and identifying the most critical areas of a business is no small feat. The most advisable approach is a cautious one that focusses on restore, scan, verify.
Looking ahead, designing in procedural security drills like Zero Trust policies and reliable firewalls will help fortify data from the outside world. For security leaders watchful about how the market is in conversation with data protection, the mental imagery around policies that focus on cyber hygiene and clean data point to a market where ransomware is a threat to the overall health of a business.
Immutable Backups
Immutability is popular in the storage world right now as it refers to a copy of data that is either encrypted or fixed. This means that your data cannot be changed, edited, or mutated.
Immutable data acts as a kind of assurance that at least a copy of your data will remain recoverable and secure against most disasters. Immutability might be a defence against human error as much as it can help recover faster during a ransomware attack.
Traditional backup and recovery systems are now being targeted by bad actors. Where markets have advancements in malware innovation, hackers are sharpening their attacks to focus not only on production systems, but on breaching a business’ safety net too. That’s why immutability matters more than ever. With fixed data backups, businesses can safeguard their workloads against a range of threats, whether external or internal.
Whether through column inches, a competitor, or a water-cooler conversation, immutability as a material solution for data backup and restoration is gaining mindshare in the wider marketplace.
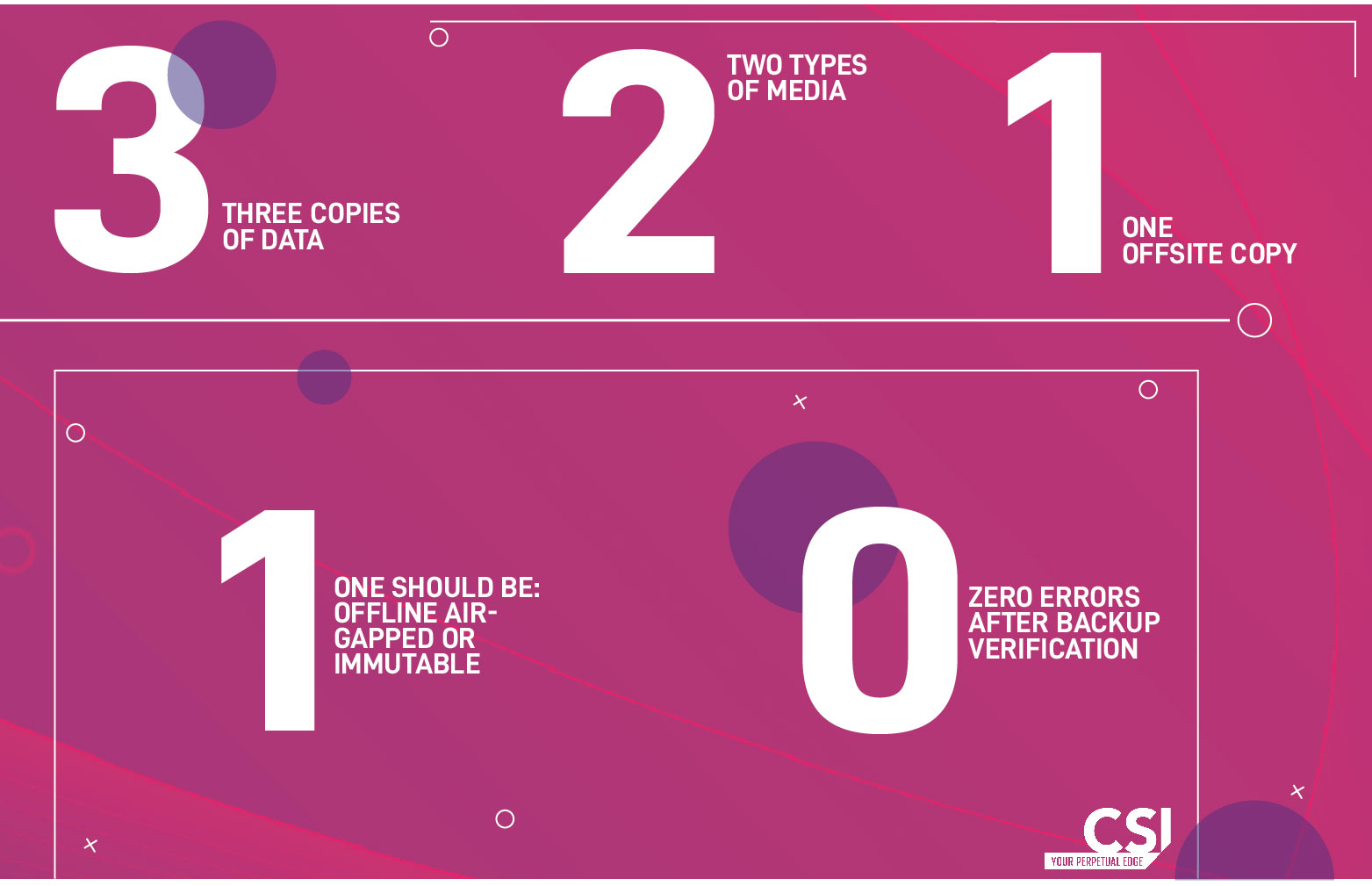
The 3-2-1-0 Backup Rule
Recoverability, in fact, is a numbers game.
The 3-2-1 rule by Veeam is a robust, advisable strategy for data protection and backup. As a guiding, bespoke security principle, 3-2-1 simplifies a modernised and, importantly, resilient approach to conceptualising your backup strategy.
According to the rule, there should be three copies of data spread across two different media with one copy that’s offsite. Different storage media types might include hard drive, tape, or the cloud. Where at least one backup copy should be stored off-site, this will ensure protection against localised disasters.
Veeam’s 3-2-1 guidance is practical because:
- it addresses almost every disaster scenario;
- it is not dependent on any single technology or product.
Following this backup guidance, businesses can anticipate minimised failures during data restoration after a breach. The end goal is always reliable recoverability and, here, we have captured the safest route to ensure backups remain resilient against modern malware.
Planning for Disaster Scenarios
During the global pandemic, and as remote workers acclimatised to new ways of working creatively from outside the protection of corporate offices, system vulnerabilities and ‘back doors’ became more open to bad actors.
Recoverability from almost any disaster can be proactively strategised. Using Zero Trust principles to silo parts of your technology stack, for example, will blunt spreading infections, slowing down the lateral movement of ransomware. Another step-change in addressing business continuity and disaster recovery at the same time is the smart use data backups to secure a business’ prized workloads.
Business continuity asks corporate leadership to imagine the aftermath of a disaster and how a business will respond on the road to recovery. How do you condense the time you are offline? How do you plan on mitigating the gross cost of ransomware as it spreads? Are my ‘crown jewels’ really safe?
Backup and Restore with CSI
CSI Group – across its global offices – works with clients internationally every day to understand, mitigate and manage the threat of ransomware.
Our team of accredited security specialists have designed and delivered solutions that align with the official expectations of the UK’s NCSC guidance on data backups. Critically, our philosophy is to manage your every data protection or cybersecurity need to ensure that you become a harder target for bad actors.
For a no-obligation chat with one of our specialists, get in touch today.
About the author
Read more like this

Cyber Security
Cyber Security tips and best practice
Discover top cyber security tips & lessons from industry influencers.

Cyber Security
Here’s how to outsmart increasingly complex cyber attacks
Threat detection is harder today than it was two years ago. Next year will be harder than this year. Why…

Cyber Security
What Does a Modern CISO Look Like?
With the new headlines around the role, what doe the modern CISO actually look like?
Ready to talk?
Get in touch today to discuss your IT challenges and goals. No matter what’s happening in your IT environment right now, discover how our experts can help your business discover its competitive edge.

