When Ransomware Attacks are More Expensive than the Ransom
Time to read: 10 mins
In any given month, a quick online search can generate a seemingly new cautionary tale about cyber security. Whether that’s a recent, high-profile and often costly attack, a newly detected system vulnerability, or a forecast of emergent threats, cyber security reporting has become another kind of ‘doom scrolling’ phenomena.
If you are keeping your watch by business quarters, then ransomware news starts to feel like an endless, bleak loop of cautionary tales. In 2023, cybercrime has developed into what many analysts perceived as a kind of ‘industry’. Luxury resort brand MGM was breached by social-engineering around the same time the Greater Manchester Police suffered a ransomware attack; techno-enthusiasts Tech Target reported a surge in ransomware claims in the cyber insurance market; Raconteur, meanwhile, started to wonder whether legislation could be the last bastion in regulating this type of cybercrime.
Not only is there a persistent ransomware anxiety, but as a kind of urgent business threat, there’s still so much more to learn.
EXCLUSIVE CONTENT
Ransomware’s ‘Water Cooler’ Moment
Most water-cooler conversations, now happening virtually, can focus on the challenges of ransomware, one of today’s most notorious attack verticals. As the ferocity of these attacks grow, even consumer news like Which? are talking to the everyday anxieties of this type of cybercrime. Inside a business, and in the daily lives of your consumers, ransomware appears to be a probable, costly disruption many are actively trying to circumvent.
Statistically, the volume of ransomware attacks is on the rise (again). New data reveals that a global crackdown, whilst slowing down ransomware rates in 2022, has seen a peak, or flurry, of new attacks this year. When addressing the heightened rates of ransomware, Wired acknowledges a changing attitude from cybercriminals, who have become ‘more aggressive and reckless’. The recent spate of ransomware attacks could be in part explained by geo-political tensions, especially the Russia-Ukraine conflict.
Analysis of breach data suggests that ransomware is persistent and pervasive, every bit as dangerous and relevant today as it was years ago.
How is Ransomware Different Now?
The traditional definition of ransomware can be misleading, as businesses prepare to deal with the fallout from a corrupted device or the data it had access to. As Hiscox identifies, cybercriminals are using data exfiltration techniques and ransomware to apply greater pressure on victims. Following the corruption of a device, if a ransom demand is not paid, criminals may threaten to publicise confidential data.

Ransomware attacks can be challenging – but what happens when stolen, private data is leveraged as a means to coax a payout from a victim?
Data exfiltration is a technique more ransomware actors are using to close the gap between a victim and a large ransom payout.
Data exfiltration is a pressure tactic that’s growing in popularity with ransomware attacks. Unlike traditional ransomware, exfiltration changes how we should perceive the nature of this kind of attack. Ransomware is more than just a ransom. Often referred to as double extortion, this style of attack encourages a victim to pay a ransom by using other data to create pressure, a kind of leverage, that threatens to hit a business with reputational and brand damage.
What is Data Exfiltration?
Data exfiltration is methodical insofar as going beyond traditional ransomware techniques to find greater leverage and pressure.
How does it work?
The cyber criminals first encrypt your data or block access to it, then they demand a ransom for its release. The data is effectively held hostage until the ransom is paid. Then there is a second threat: if the ransom is not paid, they will publish the data online or worse still, place it on the dark web.
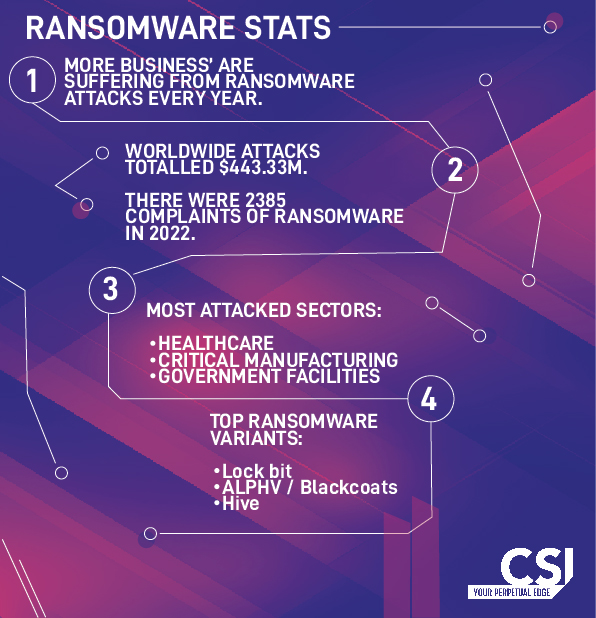
Key Ransomware Statistics & Trends
Currently the major pattern in ransomware attacks focusses on larger business, and the numbers are startling. By 2022, for example, 70% of businesses had fallen victim to a ransomware attack. With high payouts, it is not hard to imagine how ransomware has become such a widely profitable, global industry.
Looking through the data, our cyber security specialists have highlighted the key ransomware statistics every business need to know.
The Cost is More Than the Ransom
The cost of a ransomware attack is often higher than we expect.
If ransomware costs were itemised like an invoice, the ransom payment would appear as the most expensive charge. With historic ransom demands reaching an average of $1.54 million, businesses might mistakenly look at only the obvious fallout from ransomware. But the wider damage to a business could cost more in reputational harm, not to mention lost customer trust and loyalty. As tangible financial losses, businesses can expect to take a toll from downtime and consequential productivity fallout in the wider workforce. One study estimates a $5.1 million price tag in downtime losses caused by a ransomware attack. This will be compounded for different industries, where the likes of retailers would lose out on transactional costs as well.
The challenge with cybercrime is how it can harm a brand in ways that are hard to measure; after the fallout, a company will need to work long and hard to re-build trust and competitiveness in today’s fast-paced digital markets. There can be costly legal consequences associated with a breach as well. In financial services, for example, or where personal data has been exposed to risk, the regulators may impose a heavy fine.
All this means that for large, tightly regulated organisations, the full cost of a ransomware attack will far exceed the initial ransom demand.
As many attacks go unreported, the total costs of a breach may not always appear statistically accurate. This means any calculations around ransomware costs continue to be challenging.
Who is the (Main) Target of Ransomware?
The countries reporting the largest number of attacks in 2022 included the US, UK, Canada, Germany, and Italy.
Where are attacks most likely? IC3 statistics put the financial services sector, IT, Government, and critical Manufacturing (including Utilities) at the top of the list of industries likely to be attacked by ransomware.
Why? Because these organisations have the most to lose in terms of reputation in addition to the fact that they hold particularly valuable data. These are also identifiable targets due to the impact an attack could have on a country and the disruption it would cause.
It is important for all businesses to have a plan ready in case of an attack, and at a higher level, governments are looking at ways to prevent, if not regulate, attacks. The Institute for Security and Technology recommends regulating cryptocurrencies more closely, to make it harder for criminals to collect their payments.
At CSI, our advice is to have a robust cyber security defences and policies in place.
The best weapons to protect against ransomware include:
- AI-based detection and response controls
- Protection within the network / segmentation of the networks
- Run the latest version of the OS
- Instil strict back-up discipline
- Use Zero Trust security and multi-factor authentication
- Manage password policies
- Train users in network hygiene and to recognise potential threats, e.g phishing simulations

You’ve Been Attacked. What Should You do Next?
UK authorities do not recommend paying the ransom as this validates the ransomware “business model”, and it encourages criminals to continue the practice.
Critically, paying the ransom doesn’t necessarily mean that any stolen data will be safely returned. Some businesses have managed to negotiate successfully with hackers, in some instances reducing the ransom payout, where others haven’t. No two negotiations have been the same. In other cases, organisations have managed to restore their data from a backup.
The No More Ransom initiative, a project by the High Tech Crime Unit of the Netherlands Police with Europol and some anti-virus providers, is working to help companies regain control of their data and offers some useful decryption tools.
In all cases the authorities agree that it’s essential to report the event to the national authorities such as the US IC3 or the UK’s Cyber Security Centre so that they can investigate the source. This helps their joint efforts to combat ransomware worldwide.
A preventative approach to ransomware is still considered best practice. So, what does this look like?
CSI’s Ransomware Protection
As mentioned, the best protection against ransomware is a well-designed preventative security plan. We know that maintaining cyber defences isn’t simple or easy, that’s why we design, deliver and execute advanced ransomware protection.
Find out more here, or get in touch with one of our specialists today.
About the author
Ready to talk?
Get in touch today to discuss your IT challenges and goals. No matter what’s happening in your IT environment right now, discover how our experts can help your business discover its competitive edge.
